I used my gimpy drawing skills to make a diagram describing how 6to4 works. This is what that 2002:[something] address you may have noticed on your Windows Vista/7 machine. Those of you at WWU probably all have this because we're on publicly routeable IP addresses. 6to4 uses AnyCast to accomplish what it does. It can be tricky to wrap your head around since it is also a stateless protocol. Anyway, here is a picture worth a couple hundred words:
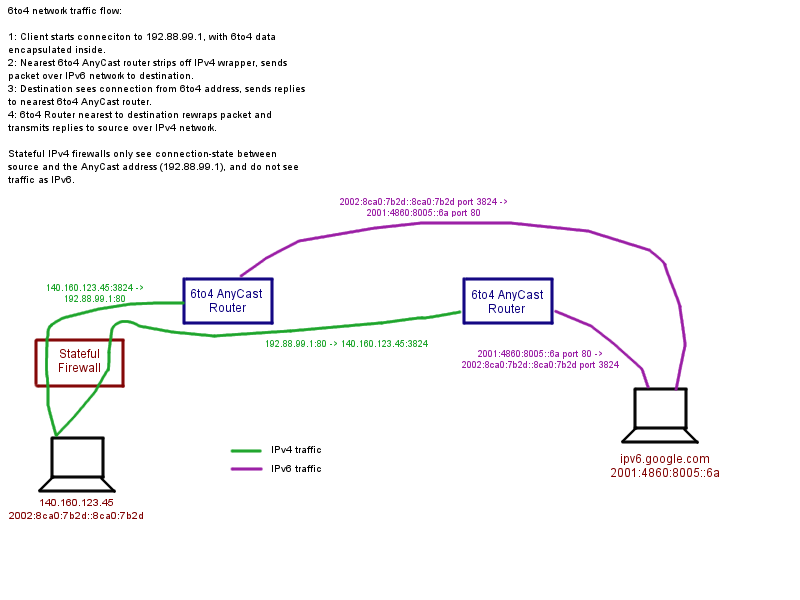
For those that don't load images, here is the traffic path between a client at 140.160.123.45 talking over 6to4 to ipv6.google.com:

For those that don't load images, here is the traffic path between a client at 140.160.123.45 talking over 6to4 to ipv6.google.com:
- Client starts a TCP session with the 6to4 AnyCast address 192.88.99.1, with an encapsulated IPv6 packet destined for 2001:4860:8005::6a.
- The nearest 6to4 AnyCast router strips off the IPv4 wrapper and forwards the formerly encapsulated packet to 2001:4860:8005::6a
- The server at 2001:4860:8005::6a sees an incoming connection from 2002:8ca0:7b2d::8ca0:7b2d, replies with ACK packet.
- As the ACK packet has 2002 prefix, it is forwarded to the 6to4 router nearest to the source which encapsulates the packet within an IPv4 packet, with a Source address of 192.88.99.1 and sends it on to 140.160.123.45
- Client receives ACK packet from 192.88.99.1, sends SYN ACK to 192.88.99.1